Updates - October 2018
| Version | Start Date | End Date | Data |
|---|---|---|---|
| ATT&CK v3 | October 23, 2018 | April 29, 2019 | v3.0 on MITRE/CTI |
Table of Contents
Transition from MediaWiki
The MediaWiki version of ATT&CK was moved to attack-old.mitre.org and will remain up until the end of January 2019. The old website will not be receiving content updates during this timeframe, so you will need to use the new website and STIX/TAXII to get the most up-to-date ATT&CK information.
Consolidated Technique and Software IDs
As of the October 2018 update all techniques across Enterprise ATT&CK, PRE-ATT&CK, and Mobile will have the same T#### numbering scheme. Existing PRE-ATT&CK and Mobile technique IDs have been converted over to the Enterprise IDs. Links to specific pages on the old wiki or to the new site with the old IDs will hit pages that redirect to the appropriate technique page.
Mobile software IDs were converted to the Enterprise format of S####.
NOTE: If you have created layers for the ATT&CK Navigator that include PRE-ATT&CK or Mobile ATT&CK techniques, you will need to update your layer files to use the new ATT&CK technique IDs.
Tactic IDs
Tactics have been given ID numbers formatted as TA####.
Mobile Mitigation IDs
Mobile migitations have been given ID numbers formatted as M####.
Versioning
We've implemented a versioning system to all ATT&CK objects (techniques, groups, software, Mobile mitigations) to enable better tracking of incremental changes to existing ATT&CK content. The system will consist of a MAJOR.MINOR number. All objects will start at version 1.0 with the October release.
Techniques
Major version changes
- Name change
- Technique scope change - Change in definition resulting in broadening or focusing the scope of the technique
Minor version changes
- Minor descriptive information - technical information, examples, detection, mitigation, references
- Metadata change - platform, permissions, data sources, defense bypassed, etc.
Groups
Major version changes
- Adding or changing associated group or software
- Big changes to description and scope of a group
Minor version changes
- Relationship to new techniques or software
- New references
Software
Major version changes
- Adding or changing an associated group or software
- High level description or information changes
- Metadata change (type)
Minor version changes
- Relationship to new techniques or software
- New references
Mobile Mitigations
Major version changes
- Name change
- Scope, description, or information changes
Minor version changes
- Metadata change
- Relationship to new techniques
- New references
In addition, the ATT&CK Matrix view of techniques within an ATT&CK domain will be timestamped with the last change that impacts its structure and organization which will act as a version number for it.
Techniques
Enterprise
New techniques:
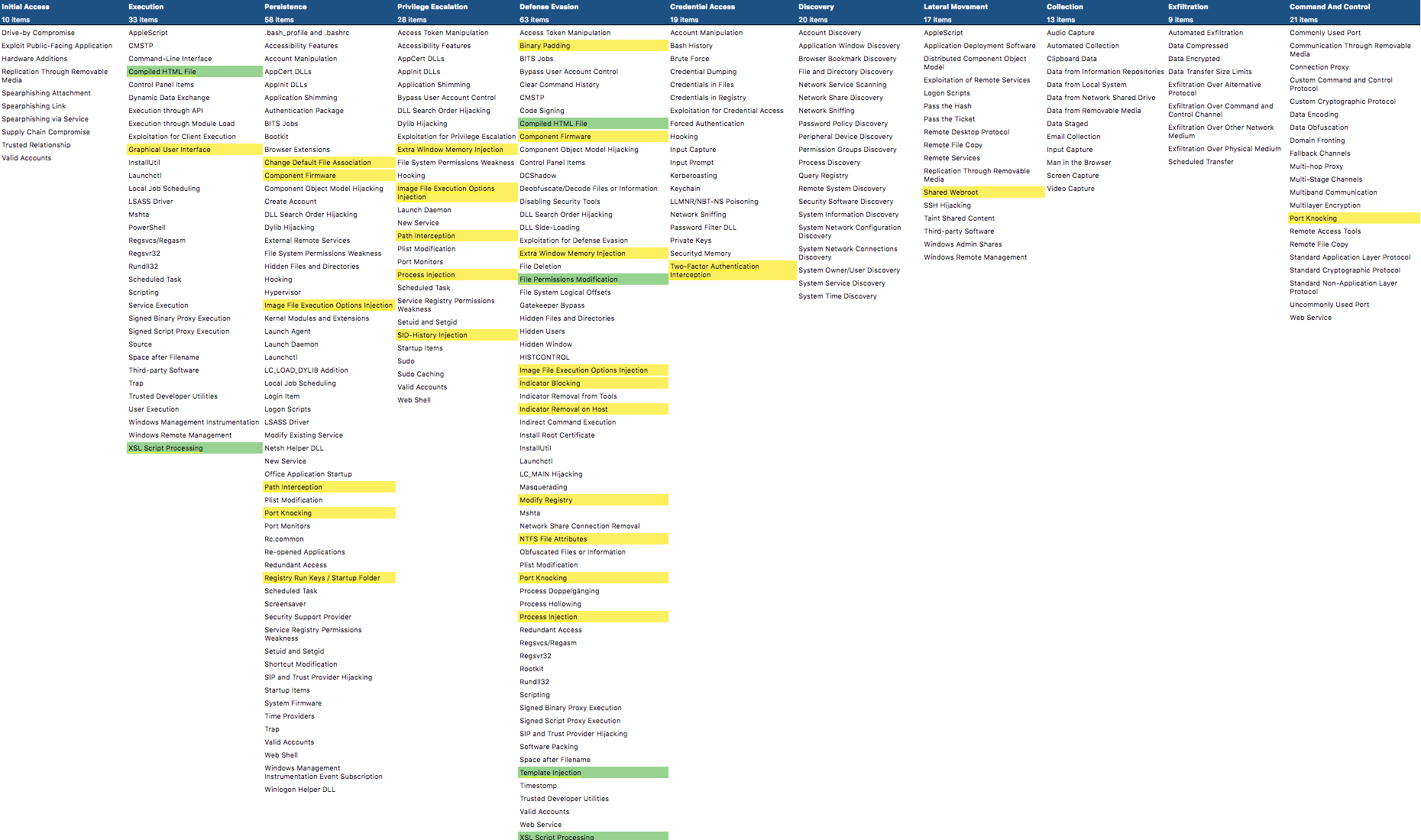
Technique Changes:
- Port Knocking
- Modify Registry
- SID-History Injection
- Graphical User Interface
- Image File Execution Options Injection
- Registry Run Keys / Startup Folder
- NTFS File Attributes
- Indicator Removal on Host
- Indicator Blocking
- Component Firmware
- Binary Padding
- Shared Webroot
- Two-Factor Authentication Interception
- Change Default File Association
- Path Interception
- Extra Window Memory Injection
- Process Injection
You can view the new and changed enterprise techniques in the ATT&CK Navigator by checking out the layer file we made available here. You can also check out a preview of the changes below! New techniques are green, and changed techniques are yellow.
PRE-ATT&CK
No changes
Mobile
The Obtain Device Access Matrix was collapsed into an Initial Access tactic to match the formatting of Enterprise.
The Network-Based Effects Matrix was consolidated into two tactic categories: Network Effects and Remote Service Effects.
Technique Additions and Changes:
- Deliver Malicious App via Authorized App Store created to consolidate several techniques in the old tactic
- Deliver Malicious App via Other Means created
- Drive-by Compromise renamed from Malicious Web Content
- Exploit via Radio Interfaces created to consolidate Exploit Baseband Vulnerability and Malicious SMS Message
- Install Insecure or Malicious Configuration created
- Supply Chain Compromise created to consolidate several techniques in the old tactic
Updated Content:
You can view the new and changed mobile techniques in the ATT&CK Navigator by checking out the layer file we made available here.
Groups
APT34 and OilRig were combined due to additional reporting increasing confidence in the overlap
- Dark Caracal
- Orangeworm
- Honeybee
- APT19
- Dragonfly 2.0 (split from Dragonfly due to reexamination of sources leading to assessment that these are better tracked as two groups)
- Rancor
- Thrip
- Leafminer
- Gorgon Group
- DarkHydrus
- Cobalt Group
Software
Enterprise
Poison Ivy and Darkmoon pages were combined into Poison Ivy
Mobile